Social EngineeringSocial engineering is the art of manipulating people so that they give up confidential information.
People are often the weakest point in security systems, social engineering focuses on people rather than on technology, as the weak point in any security system. There are many different ways to manipulate people to surrender their confidential information or data.
There are many threats to network security. Most target computers and communications software, but many target far weaker links: those who use them. A study shows that human error was the main root cause of all security breaches in networks. The biggest problems were failure to follow general policies and procedures, general carelessness, and a lack of knowledge of threats. Some of the methods used to breach network security need no knowledge of programming or computers. These are low-tech con-tricks, referred to as social engineering, aimed at manipulating vulnerable people into disclosing their personal information. Blagging is creating and using an invented scenario (the pretext) to engage a targeted victim in a manner that increases the chance the victim will divulge information or perform actions that would be unlikely in ordinary circumstances. Examples are the Nigerian Prince scam and more recently the emails from friends who have been mugged (in a foreign country) and need you to send money.
Phishing is a technique of fraudulently obtaining private information, often using email or SMS. It might look like it comes from a bank or other legitimate business. The criminal hopes that the user will give away some important information eg by following a link to a false website and logging in with their ID.
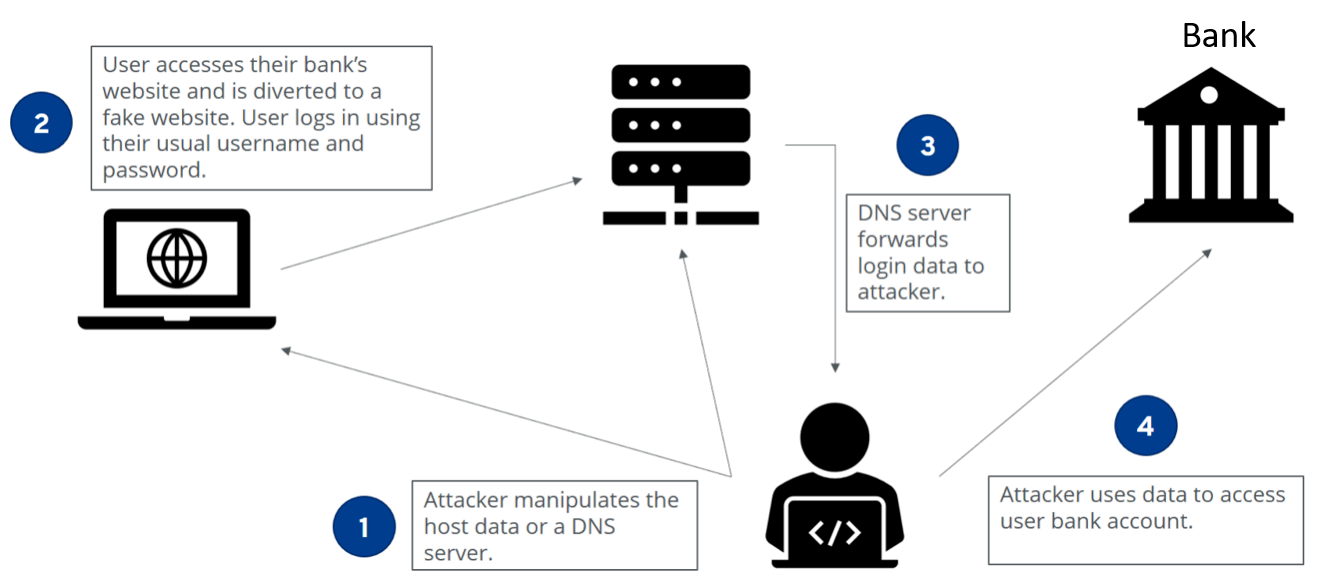
Pharming is a cyber attack intended to redirect a website's traffic to another, fake site. This can be done by hacking a DNS server or redirecting your computer electronically.
Shouldering is a simpler way of obtaining people's Passwords or PIN numbers. Criminals just stand behind and watch what you type.
Questions: Exercises: Ex. 1 Identify social engineering methods according to situations Exam questions: | |
|
| |
| Просмотров: 1911 | | |
| Всего комментариев: 0 | |